How to Send Events to Splunk in Docker Using Postman

Running Splunk locally in Docker? This guide shows you how to manually send events using Postman and the HTTP Event Collector (HEC).
Step 1 - Setup Splunk Using Docker Compose
We’ll start by launching a Splunk instance using the following docker-compose.yml:
version: '3'
services:
splunk:
image: splunk/splunk:latest
container_name: splunk
hostname: splunk
environment:
- SPLUNK_START_ARGS=--accept-license
- SPLUNK_PASSWORD=password123
ports:
- "8000:8000" # Splunk UI
- "8088:8088" # HTTP Event Collector (optional)
volumes:
- splunk-data:/opt/splunk/var
restart: always
volumes:
splunk-data: Save the file as docker-compose.yml
Open a terminal and navigate to the folder containing this file.
Run:
docker-compose up -dThis will download the Splunk Docker image and start a container with the Splunk web interface accessible at:
http://localhost:8000Log credentials:
- Username:
admin - Password:
password123(or whatever you set in thedocker-compose.ymlfile).
Step 2 - Enable and Configure the HTTP Event Collector (HEC)
Open Splunk Web and login:
http://localhost:8000Go to Settings > Data Inputs.
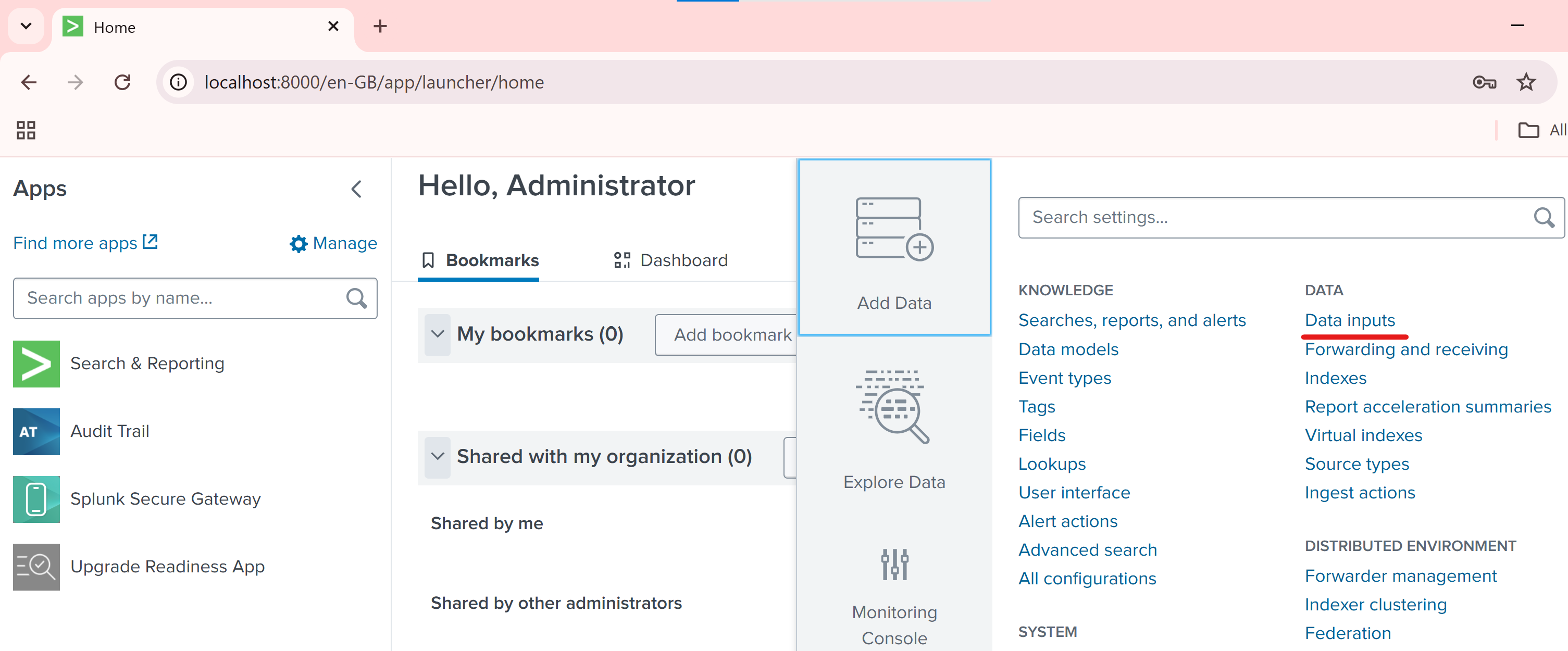
Click HTTP Event Collector.
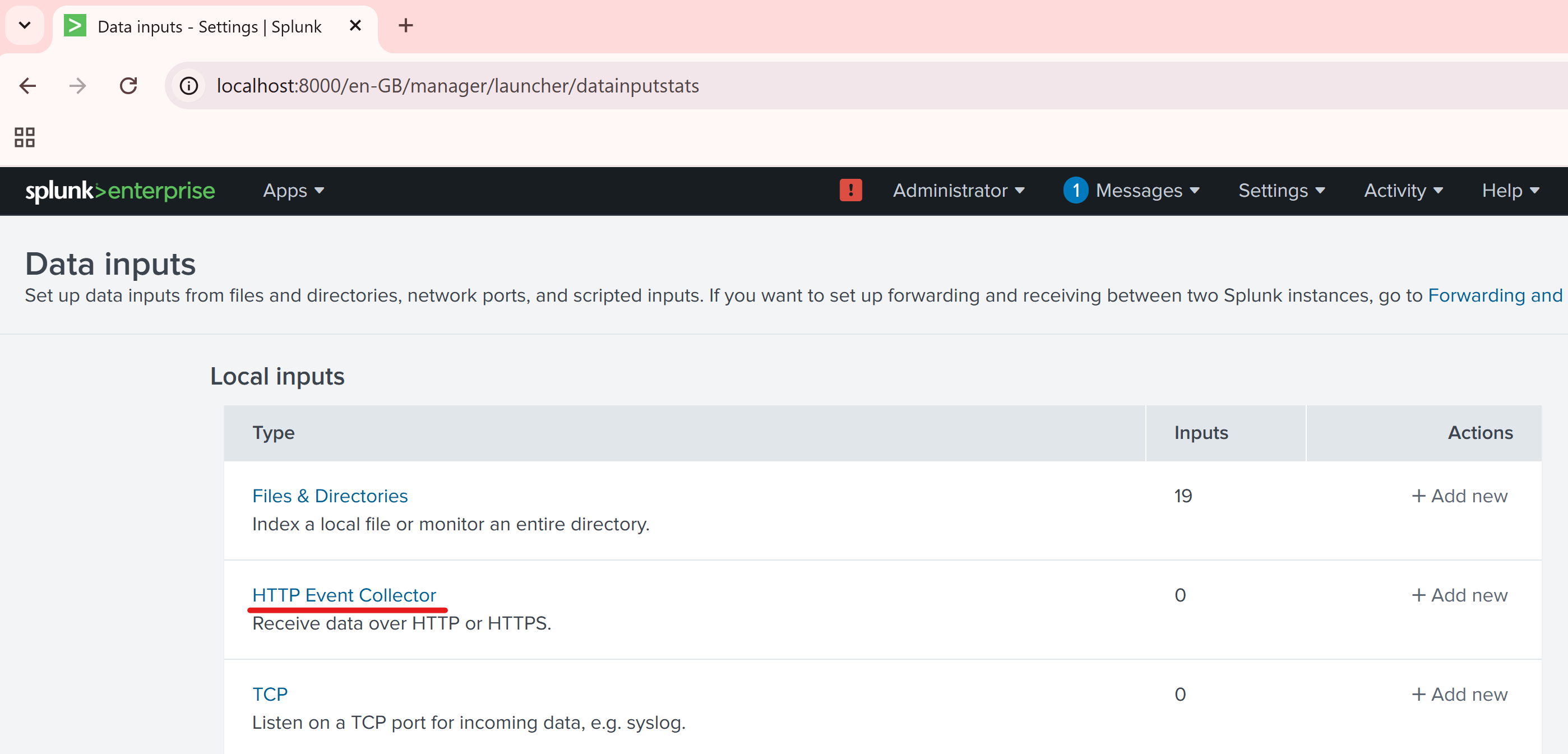
Click New Token.
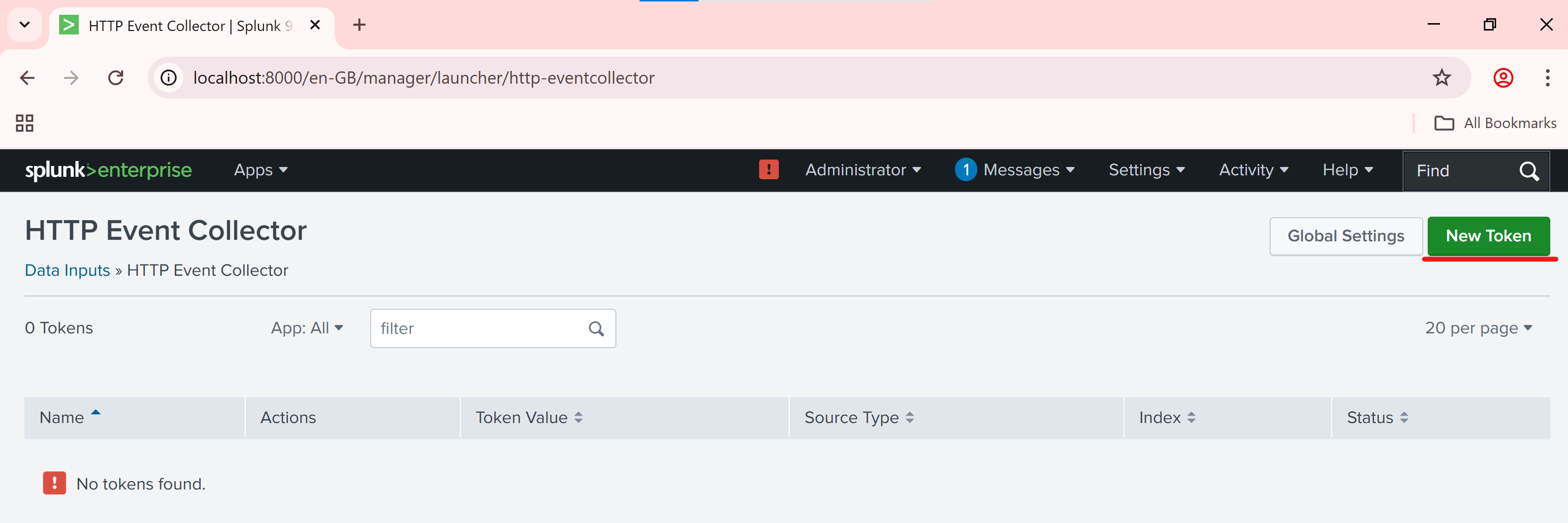
Name your token (e.g., PostmanToken) and click Next.
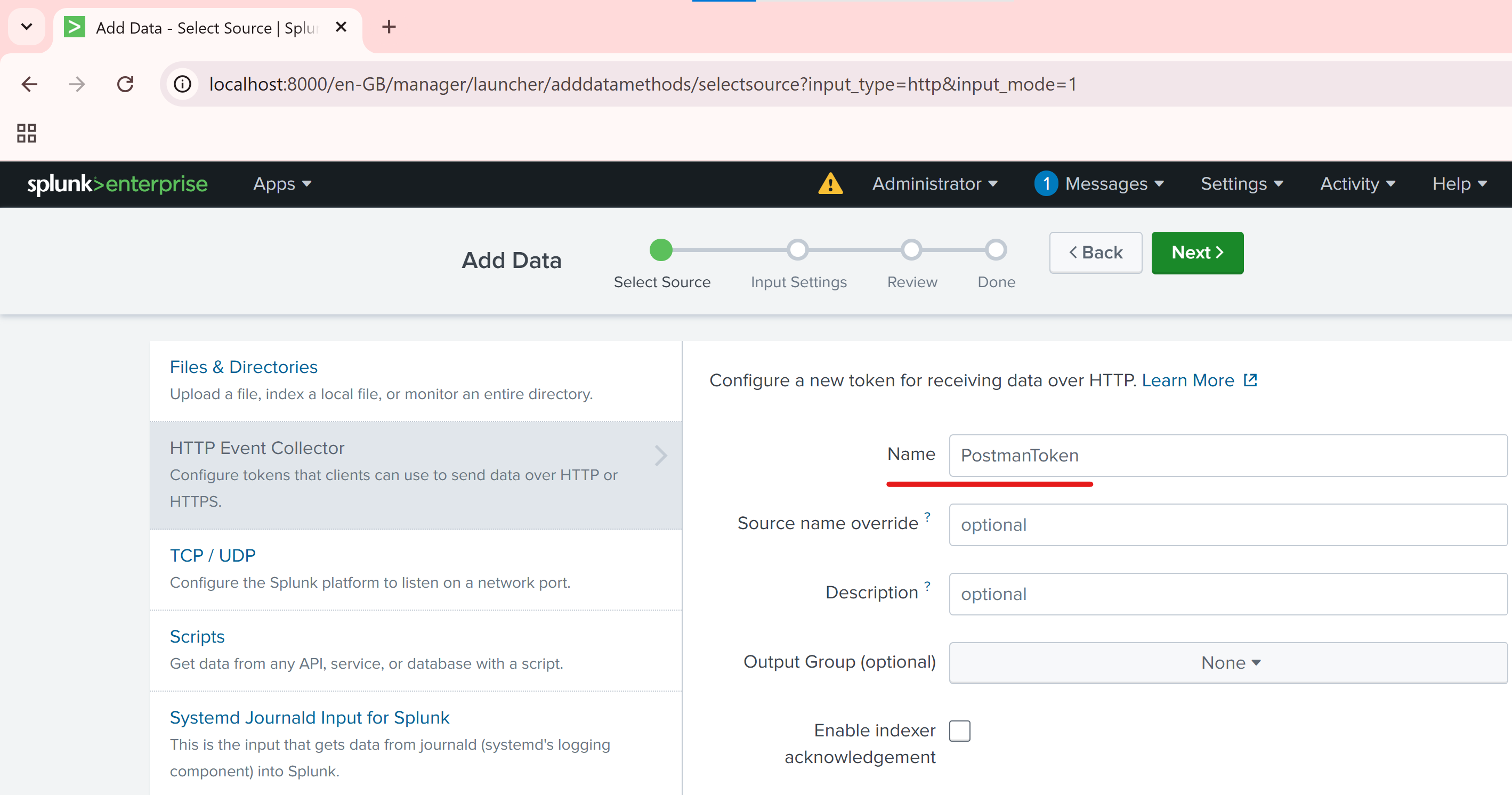
Select a source type and index (or leave defaults).
Click Review, then Submit.
Once the token is created, you’ll get a Token Value — copy this! You'll use it in Postman.

Step 3 - Send an Event to Splunk Using Postman
Now we’ll send a POST request to Splunk using the token you created.
Endpoint: https://localhost:8088/services/collectorHeaders:
| Key | Value |
|---|---|
| Authorization | Splunk <YourToken> (e.g., Splunk 9b0a3af4-1246-4b5f-9cb3-5197b82ddd46) |
| Content-Type | application/json |
Body (JSON):
{
"event": "Hello from Postman",
"sourcetype": "json",
"index": "main"
}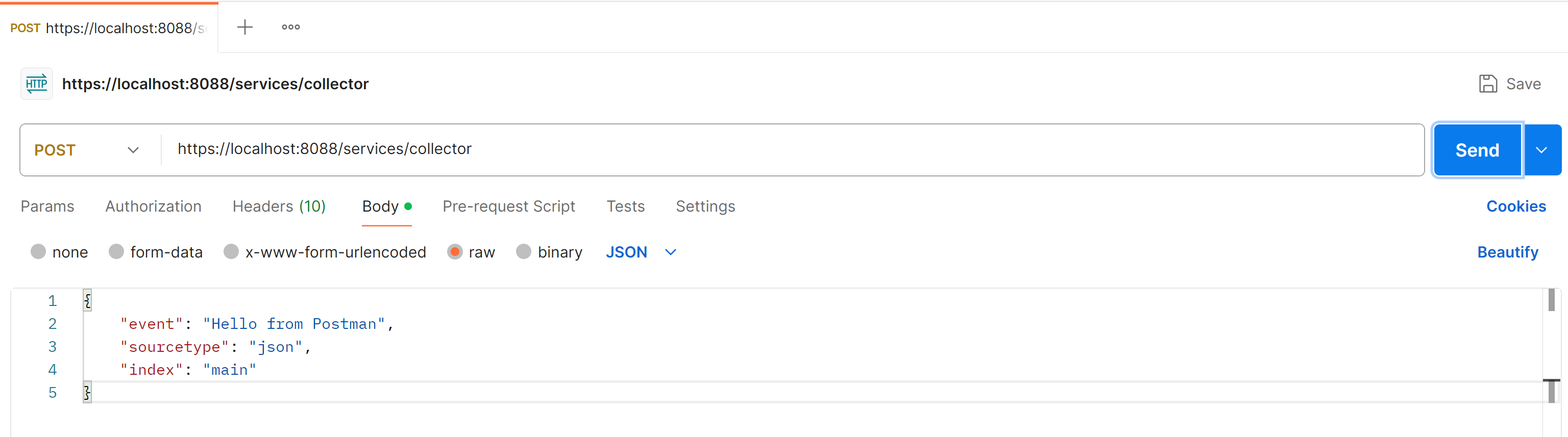
Hit Send and a 200 OK response is returned.
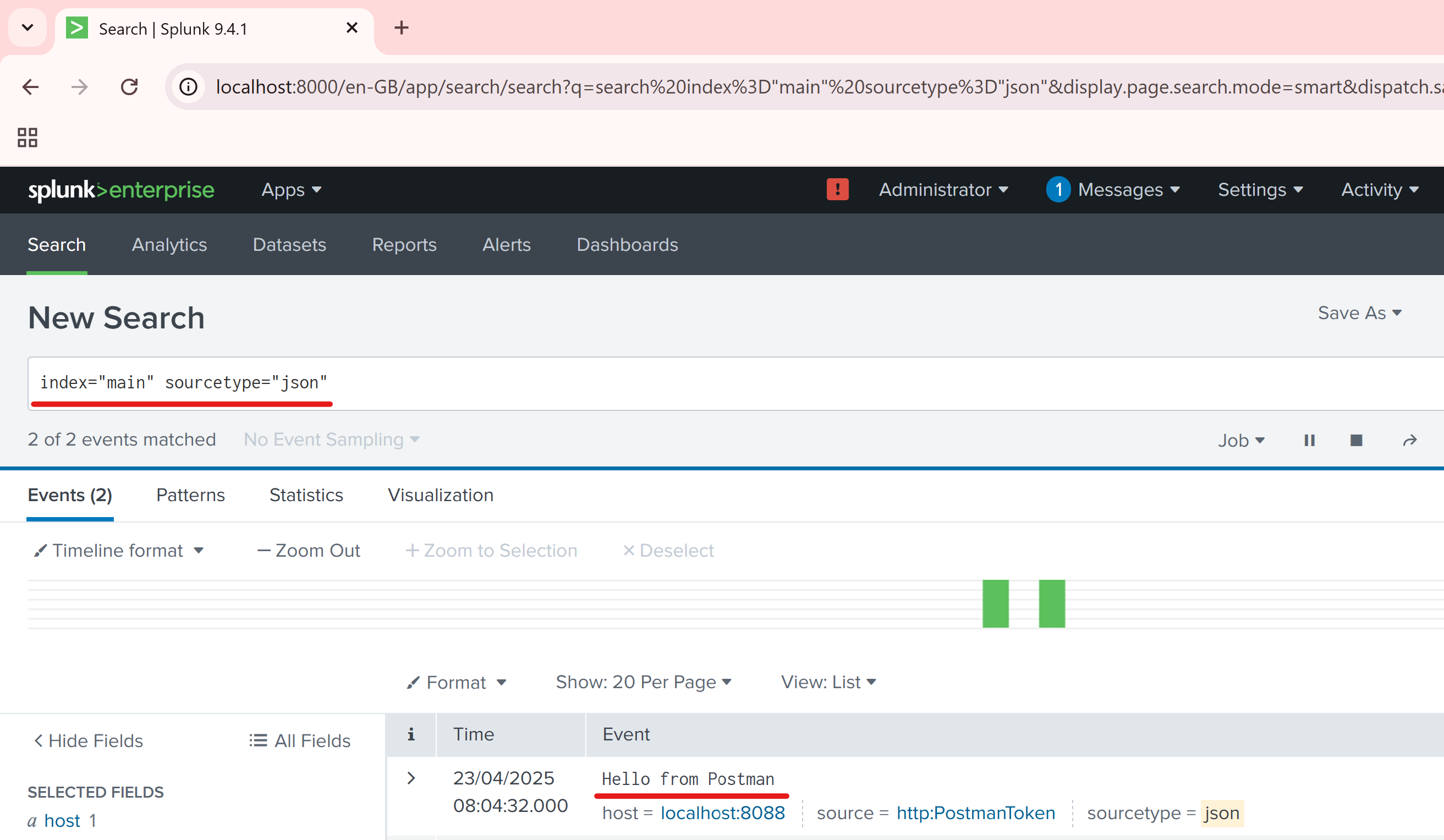
Step 4 - Verify the Event in Splunk
Go back to Splunk Web:
http://localhost:8000Click Search & Reporting.
Run a search:
index="main" sourcetype="json"The event has landed in Splunk.